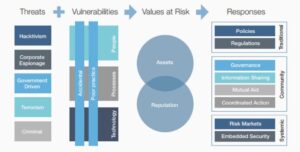
In 2015 the World Economic Forum developed a preliminary framework for a statistical model CIO’s and other executives can use to begin to quantify the financial impact of cyber threats. Better understanding Value at Risk (VAR) because of Cyber incidents was identified as needing more attention.
Each type of threat may well have core VAR attributes but some will have greater VAR consequences (e.g. a destructive denial operation). What we know about threat is that all variants of threat exist at the same time and it is just the driver to act on that knowledge varies in each group.
The IRM approach to developing scenarios for exercising or Red Teaming takes into account the type of investment in time and technology an attacker might be prepared to spend for a particular outcome. So for instance, research of vulnerabilities by crime groups might be limited to a few days or weeks whereas at the state level it would often be months or sometime years in development.
In understanding VAR it is helpful to consider the wider possible scenarios under which hostile groups deploy their techniques. At state and military levels, planning considerations factor in 5 typical outcomes being sought (the 5 Ds);
- Intent to Deceive their target
- Intent to Degrade their target’s capabilities
- Intent to Deny their target’s ability to undertake certain functions
- Intent to Disrupt their target’s operations more widely (in some cases to gain financial outcomes)
- Intent to Destroy their target’s existing capabilities.
Why spending that little bit extra is so important
The North Korean Lazarus group in their attempted Billion-dollar heist against Bangladesh’s National bank used this type of planning in 2016. This attack was moments from complete success but still resulted in £millions in financial losses.
IRM can offer a proposed price range which aims at reflecting the types of investment from low level crime groups looking for modest financial gain (albeit that could be a significant amount) through to more sophisticated crime groups looking for significant financial benefit (e.g. Lazarus in nature). Ransomware could manifest itself as an outcome at all levels these days given there are commodity crime tools available on line.
So when we offer our proposal it is focussed at a level where we feel more organised crime groups might operate and invest time and effort in establishing its options for exploitation within your business for financial gain.
As a CHECK with close relations to the UK National Cyber Security Centre, assurance standards and continuous tracking of UK regulatory requirements. IRM seek to ensure that the work undertaken is of the highest quality in support of reporting requirements that the organisation might have under its licence to operate.
The Red Team engagement is aimed at identifying opportunities in each of the 4 reportable incident types identified in the current FCA regulations.
WHAT THE FCA SAY
FCA recent updates in response to growing Cyber risks and the need to evaluate operational resilience
The FCA has continued to evolve its regulatory views on acceptable levels of assurance and operational resilience by service providers. New operational resilience requirements for firms were issued in March this year. By March 2022 this requires banks, building societies, PRA-designated investment firms, insurers, Recognised Investment Exchanges, Enhanced scope Senior Managers and Certification Regime firms, and entities authorised and registered under the Payment Services Regulations 2017 and Electronic Money Regulations 2011 to have:
- identified your important business services that, if disrupted, could cause intolerable harm to consumers of your firm or risk to market integrity, threaten the viability of firms or cause instability in the financial system
- set impact tolerances for the maximum tolerable disruption to these services
- carried out mapping and testing to a level of sophistication necessary to identify important business services, set impact tolerances and identify any vulnerabilities in its operational resilience
- conducted lessons learnt exercises to identify, prioritise, and invest in your ability to respond and recover from disruptions as effectively as possible
- developed internal and external communications plans for when important business services are disrupted
- prepared self-assessment documentation
Under Principle 11 of the FCA’s Principles for Business the core elements of collaboration and disclosure of material incidents which fall into certain key categories. Incidents that:
- results in a significant loss of data
- results in the unavailability or control of your IT systems
- affects a large number of customers
- results in unauthorised access to your information system
If you feel you’d like to explore how IRM can help your business with a Red team engagement, here is how you find out more: please contact us on 01242 225200 or email sales@irmsecurity.com

