Malicious software (known as malware) continues to evolve over time.
In the past, malware predominantly came in the form of a single executable file with self-contained functionality. Often internet miscreants would use a form a malware known as a Remote Access Trojan (RAT) to remotely control a victims computer system. Examples of this type of malware, include Sub7 dating back to 1999.
Anti-Virus software only improves over time to get better at detecting this type of malicious software. But this is a cat and mouse game, and as security controls have gotten better attackers have developed new forms of malware to evade detection.
In this article, we’re going to be looking at the Anti-Malware Scan Interface (AMSI), and how it helps protect your computer from malicious software.
How does Anti-Virus Software Work?
Modern anti-virus software relies on a large number of techniques to detect Malware. The primary method it uses it scanning content for “known bad” code.
We can demonstrate how this works by looking at a common remote access trojan utilised by attackers, Covenant.
We can scan a copy of a Covenant agent using a tool called ThreatCheck. This tool shows us which corresponding data in the Covenant executable Windows Defender Anti-Virus objects to;
| ThreatCheck.exe -f Downloads\Grunt.bin -e AMSI
[+] Target file size: 31744 bytes [+] Analyzing… [!] Identified end of bad bytes at offset 0x6D7A 00000000 65 00 22 00 3A 00 22 00 7B 00 32 00 7D 00 22 00 e·”·:·”·{·2·}·”· 00000010 2C 00 22 00 74 00 6F 00 6B 00 65 00 6E 00 22 00 ,·”·t·o·k·e·n·”· 00000020 3A 00 7B 00 33 00 7D 00 7D 00 7D 00 00 43 7B 00 :·{·3·}·}·}··C{· 00000030 7B 00 22 00 73 00 74 00 61 00 74 00 75 00 73 00 {·”·s·t·a·t·u·s· 00000040 22 00 3A 00 22 00 7B 00 30 00 7D 00 22 00 2C 00 “·:·”·{·0·}·”·,· 00000050 22 00 6F 00 75 00 74 00 70 00 75 00 74 00 22 00 “·o·u·t·p·u·t·”· 00000060 3A 00 22 00 7B 00 31 00 7D 00 22 00 7D 00 7D 00 :·”·{·1·}·”·}·}· 00000070 00 80 B3 7B 00 7B 00 22 00 47 00 55 00 49 00 44 ·?³{·{·”·G·U·I·D 00000080 00 22 00 3A 00 22 00 7B 00 30 00 7D 00 22 00 2C ·”·:·”·{·0·}·”·, 00000090 00 22 00 54 00 79 00 70 00 65 00 22 00 3A 00 7B ·”·T·y·p·e·”·:·{ 000000A0 00 31 00 7D 00 2C 00 22 00 4D 00 65 00 74 00 61 ·1·}·,·”·M·e·t·a 000000B0 00 22 00 3A 00 22 00 7B 00 32 00 7D 00 22 00 2C ·”·:·”·{·2·}·”·, 000000C0 00 22 00 49 00 56 00 22 00 3A 00 22 00 7B 00 33 ·”·I·V·”·:·”·{·3 000000D0 00 7D 00 22 00 2C 00 22 00 45 00 6E 00 63 00 72 ·}·”·,·”·E·n·c·r 000000E0 00 79 00 70 00 74 00 65 00 64 00 4D 00 65 00 73 ·y·p·t·e·d·M·e·s 000000F0 00 73 00 61 00 67 00 65 00 22 00 3A 00 22 00 7B ·s·a·g·e·”·:·”·{
|
Looking at the Covenant agent source code, we can see the bytes Windows Defender objects to relate to the following line of code.
| string MessageFormat = @”{{“”GUID””:””{0}””,””Type””:{1},””Meta””:””{2}””,””IV””:””{3}””,””EncryptedMessage””:””{4}””,””HMAC””:””{5}””}}”; |
Modifying this code may allow us to bypass the on disk detection checks. This is often an effective technique, but can be an arduous process depending on how many detections are in place.
Attackers normally aim to go for the path of least resistance, and have moved to alternative techniques that have a lesser amount of coverage.
The Rise of Fileless Attacks
Fileless malware typically refers to malware that does not leave an on disk footprint.
Script Based Malware
Using scripting languages as opposed to native binaries has been a favoured approach for attackers over the past few years. Malicious PowerShell code is probably the best example of this.
PowerShell is a automation and configuration tool that is available for multiple platforms, but is also built into modern versions of Microsoft Windows. Natively, PowerShell provides all the functionality an attacker needs to conduct their operations.
Memory Based Malware
As discussed, in the past malware would predominantly be a single executable file. This file could be easily analysed by anti-virus software to determine if it contained known bad code. Memory based malware uses techniques such as process injection to execute code directly in memory without touching disk. A lot of Anti-Virus products do not scan memory due to the high performance impact. If they do scan memory, it is often done infrequently.
How does AMSI work?
To combat fileless malware, the Anti-Malware Scan Interface was developed by Microsoft. AMSI takes content from scripting interpreters or other operating system components and sends them to the installed Anti-Virus software for analysis.
In Windows, the following components integrate with AMSI;
- User Account Control, or UAC (elevation of EXE, COM, MSI, or ActiveX installation)
- PowerShell (scripts, interactive use, and dynamic code evaluation)
- Windows Script Host (wscript.exe and cscript.exe)
- JavaScript and VBScript
- Office VBA macros
Having AMSI enabled significantly complicates matters for attackers.
In order to utilise AMSI, you need the following components;
- A supported operating system. Windows 10, and Windows Server 2016 onwards both support AMSI.
- Your Anti-Virus software needs to support AMSI. Most modern solutions do, but it’s worth verifying this is the case. In some cases it may not be operating correctly, and it is unlikely to warn you if this is not the case.
How Can I Tell AMSI is Working as Intended?
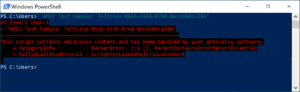
You can perform a quick check to make sure AMSI is working on your system by entering the following text in a PowerShell prompt: ‘AMSI Test Sample: 7e72c3ce-861b-4339-8740-0ac1484c1386’
If AMSI is working correctly, you should receive an alter stating the content was blocked:
Closing Thoughts
We feel that every organisation should implement AMSI where possible. It provides another layer of defence against modern malware attacks. Bear in mind, like any other control it is not infallible. There are ways to circumvent it’s operation, but it adds to an organisations defence in depth strategy.
We recommend you test the effectiveness of your security controls, to ensure they are working as intended. Penetration Testing teams are well versed in the different techniques that malicious actors utilise to compromise networks, and can carry out this assurance work.
How can IRM help protect your business?
Please contact sales@irmsecurity.com for more information.
